搭建 服务器 安装OpenLDAP的相关 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 $ yum -y install openldap compat-openldap openldap-clients openldap-servers openldap-servers-sql openldap-devel migrationtools $ tail -n 1 /etc/passwd ldap:x:55:55:LDAP User:/var/lib/ldap:/sbin/nologin $ rpm -qa | grep openldap openldap-servers-2.4.44-22.el7.x86_64 openldap-servers-sql-2.4.44-22.el7.x86_64 compat-openldap-2.3.43-5.el7.x86_64 openldap-2.4.44-22.el7.x86_64 openldap-devel-2.4.44-22.el7.x86_64 openldap-clients-2.4.44-22.el7.x86_64 $ slapd -VV @( mockbuild@x86-02.bsys.centos.org:/builddir/build/BUILD/openldap-2.4.44/openldap-2.4.44/servers/slapd /etc/openldap/slapd.conf /etc/openldap/slapd.d/* /etc/openldap/schema/* /var/lib/ldap/* /usr/share/openldap-servers/slapd.conf.obsolete /usr/share/openldap-servers/DB_CONFIG.example 默认监听端口:389(明文数据传输) 加密监听端口:636(密文数据传输) chown ldap:ldap /var/lib/ldap/DB_CONFIGOpenLDAP 2.3之后的版本取消了/etc/openldap/slapd.conf的配置方式,使用ldif文件动态配置,目前网上的文档五花八门而且缺胳膊少腿,以下参考官方文档及slapd-config(5) http://www.openldap.org/doc/admin24/slapdconf2.html http://www.openldap.org/doc/admin24/quickstart.html $ slappasswd -s 123456 {SSHA}cQb7UUcz2x6p6rB1gm9EmsVcM8Rrfp6h
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 dn: cn=config objectClass: olcGlobal cn: config olcArgsFile: /var/run/openldap/slapd.args olcPidFile: /var/run/openldap/slapd.pid dn: cn=module,cn=config objectClass: olcModuleList cn: module olcModulepath: /usr/lib64/openldap olcModuleload: accesslog.la olcModuleload: auditlog.la olcModuleload: back_dnssrv.la olcModuleload: back_ldap.la olcModuleload: back_mdb.la olcModuleload: back_meta.la olcModuleload: back_null.la olcModuleload: back_passwd.la olcModuleload: back_relay.la olcModuleload: back_shell.la olcModuleload: back_sock.la olcModuleload: collect.la olcModuleload: constraint.la olcModuleload: dds.la olcModuleload: deref.la olcModuleload: dynlist.la olcModuleload: memberof.la olcModuleload: pcache.la olcModuleload: ppolicy.la olcModuleload: refint.la olcModuleload: retcode.la olcModuleload: rwm.la olcModuleload: seqmod.la olcModuleload: smbk5pwd.la olcModuleload: sssvlv.la olcModuleload: syncprov.la olcModuleload: translucent.la olcModuleload: unique.la olcModuleload: valsort.la dn: cn=schema,cn=config objectClass: olcSchemaConfig cn: schema include: file:///etc/openldap/schema/core.ldif dn: olcDatabase=frontend,cn=config objectClass: olcDatabaseConfig objectClass: olcFrontendConfig olcDatabase: frontend dn: olcDatabase=config,cn=config objectClass: olcDatabaseConfig olcDatabase: config olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,c n=auth" manage by * nonedn: olcDatabase=monitor,cn=config objectClass: olcDatabaseConfig olcDatabase: monitor olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,c n=auth" read by dn.base="cn=root,dc=quhui,dc=com" read by * none dn: olcDatabase=hdb,cn=config objectClass: olcDatabaseConfig objectClass: olcHdbConfig olcDatabase: hdb olcSuffix: dc=quhui,dc=com olcRootDN: cn=root,dc=quhui,dc=com olcRootPW: {SSHA}cQb7UUcz2x6p6rB1gm9EmsVcM8Rrfp6h olcDbDirectory: /var/lib/ldap olcDbIndex: objectClass eq,pres olcDbIndex: ou,cn,mail,surname,givenname eq,pres,sub
导入DB_CONFIG、重新生成配置、修改目录权限并启动服务 1 2 3 4 5 6 7 8 9 10 rm -rf /etc/openldap/slapd.d/* cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG slapadd -n 0 -F /etc/openldap/slapd.d -l /usr/share/openldap-servers/slapd.ldif chown -R ldap.ldap /etc/openldap/slapd.d/*chown -R ldap.ldap /var/lib/ldap/*ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
启动 执行ldapsearch -x检查是否有如下输出 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 $ ldapsearch -x -b '' -s base'(objectclass=*)' dn: objectClass: top objectClass: OpenLDAProotDSE search: 2 result: 0 Success $ ldapsearch -x -b "cn=root,dc=quhui,dc=com"
验证用户密码 1 2 3 4 5 $ ldapwhoami -D "cn=root,dc=quhui,dc=com" -W -H ldap://127.0.0.1 -v ldap_initialize( ldap://127.0.0.1:389/??base ) Enter LDAP Password: dn:cn=root,dc=quhui,dc=com Result: Success (0)
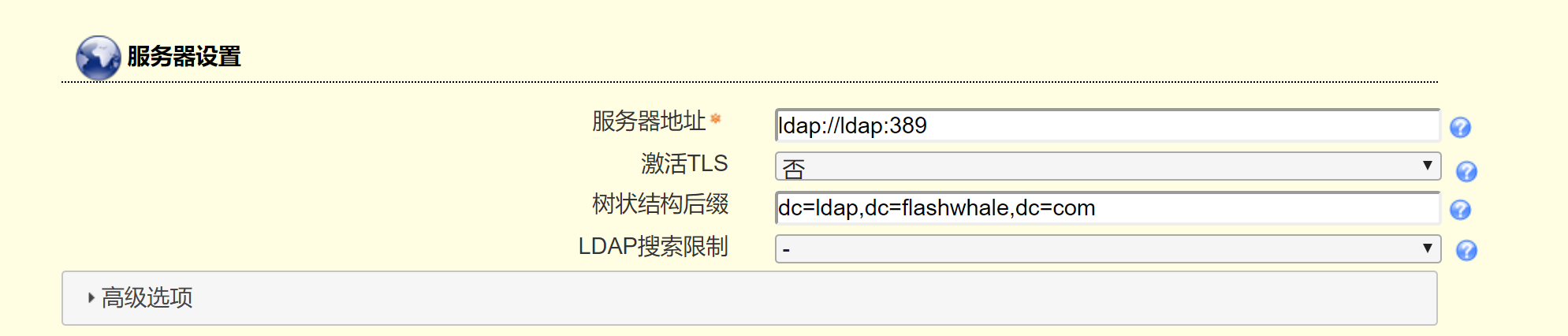
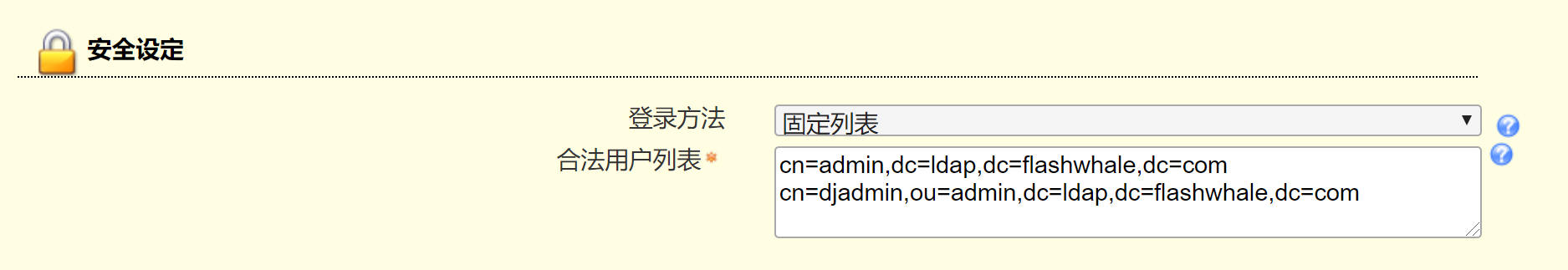
docker server 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 docker run -d --restart always \ -p 389:389 -p 636:636 \ --name ldap-server \ --env LDAP_TLS=false \ --env LDAP_ORGANISATION="flashwhale" \ --env LDAP_DOMAIN="flashwhale.com" \ --env LDAP_ADMIN_PASSWORD="djadmin" \ --env LDAP_CONFIG_PASSWORD="djadmin" \ -v /data/ldap/ldap:/var/lib/ldap \ -v /data/ldap/slapd.d:/etc/ldap/slapd.d \ osixia/openldap:1.4.0 dn dc=example,dc=org admin admin,dc=example,dc=org password admin
进入容器,验证一下是否可用 1 2 3 4 5 docker exec -it ldap-server /bin/bash ldapsearch -x -H ldap://localhost:389 -b dc=flashwhale,dc=com -D "cn=admin,dc=flashwhale,dc=com" -w djadmin
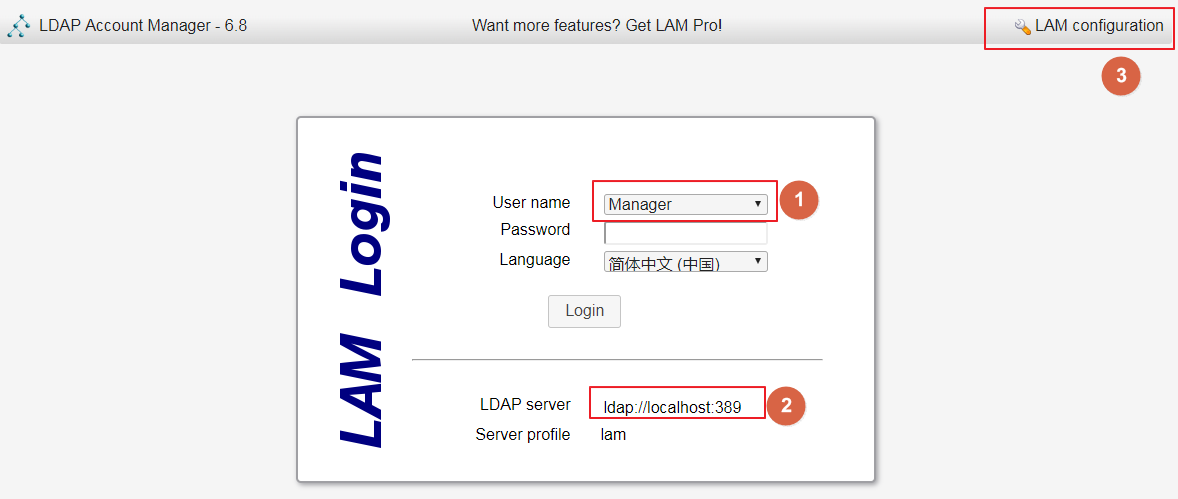
搭建ldapaccountmanager 注意:搭建ldapaccountmanager如果使用数据卷挂载要加环境变量,还要下载数据包Tar.bz2,将其config文件夹的内容用于存储卷
https://www.ldap-account-manager.org/lamcms/releases
官方又给了两个配置文件存储地方:
/etc/ldap-account-manager
/var/lib/ldap-account-manager
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 docker run -itd --rm --name lam ldapaccountmanager/lam:7.4 mkdir /data/lam -pdocker cp lam:/var/lib/ldap-account-manager /data/lam mv /data/lam/ldap-account-manager /data/lam/datadocker cp lam:/etc/ldap-account-manager /data/lam mv /data/lam/ldap-account-manager /data/lam/configchown 33:0 /data/lam/data -Rchown 33:0 /data/lam/config -Rdocker run -d \ -p 80:80 \ --name lam \ --env LAM_SKIP_PRECONFIGURE=true \ --volume /data/lam/config:/etc/ldap-account-managerg \ --volume /data/lam/data:/var/lib/ldap-account-manager \ ldapaccountmanager/lam:7.4
设置
默认密码: lam
k8s 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 kind: Service apiVersion: v1 metadata: name: ldap namespace: devops labels: app: ldap spec: ports: - name: ldap port: 389 targetPort: 389 selector: app: ldap --- apiVersion: apps/v1 kind: Deployment metadata: name: ldap namespace: devops spec: selector: matchLabels: app: ldap template: metadata: labels: app: ldap spec: terminationGracePeriodSeconds: 10 containers: - name: ldap image: osixia/openldap:1.4.0 imagePullPolicy: IfNotPresent ports: - containerPort: 389 name: tcp-389 volumeMounts: - name: ldapdata mountPath: /var/lib/ldap - name: ldapconf mountPath: /etc/ldap env: - name: SLAPD_PASSWORD value: "djadmin" - name: SLAPD_DOMAIN value: "ldap.flashwhale.com" volumes: - name: ldapdata persistentVolumeClaim: claimName: ldapdata - name: ldapconf persistentVolumeClaim: claimName: ldapconf --- kind: PersistentVolumeClaim apiVersion: v1 metadata: name: ldapdata namespace: devops annotations: volume.beta.kubernetes.io/storage-class: "alicloud-nas-fast" spec: accessModes: - ReadWriteMany resources: requests: storage: 10Gi --- kind: PersistentVolumeClaim apiVersion: v1 metadata: name: ldapconf namespace: devops annotations: volume.beta.kubernetes.io/storage-class: "alicloud-nas-fast" spec: accessModes: - ReadWriteMany resources: requests: storage: 10Gi --- kind: Service apiVersion: v1 metadata: name: ldapaccountmanager namespace: devops labels: app: ldapaccountmanager spec: ports: - name: ldap protocol: TCP port: 80 targetPort: 80 selector: app: ldapaccountmanager --- apiVersion: apps/v1 kind: Deployment metadata: name: ldapaccountmanager namespace: devops spec: selector: matchLabels: app: ldapaccountmanager template: metadata: labels: app: ldapaccountmanager spec: terminationGracePeriodSeconds: 10 containers: - name: ldapaccountmanager image: ldapaccountmanager/lam:7.2 imagePullPolicy: IfNotPresent ports: - containerPort: 80 name: http protocol: TCP volumeMounts: - name: ldapaccountmanagerconf mountPath: /var/lib/ldap-account-manager/config resources: {} env: - name: LAM_SKIP_PRECONFIGURE value: "true" volumes: - name: ldapaccountmanagerconf persistentVolumeClaim: claimName: ldapaccountmanagerconf --- kind: PersistentVolumeClaim apiVersion: v1 metadata: name: ldapaccountmanagerconf namespace: devops annotations: volume.beta.kubernetes.io/storage-class: "alicloud-nas-fast" spec: accessModes: - ReadWriteMany resources: requests: storage: 10Gi
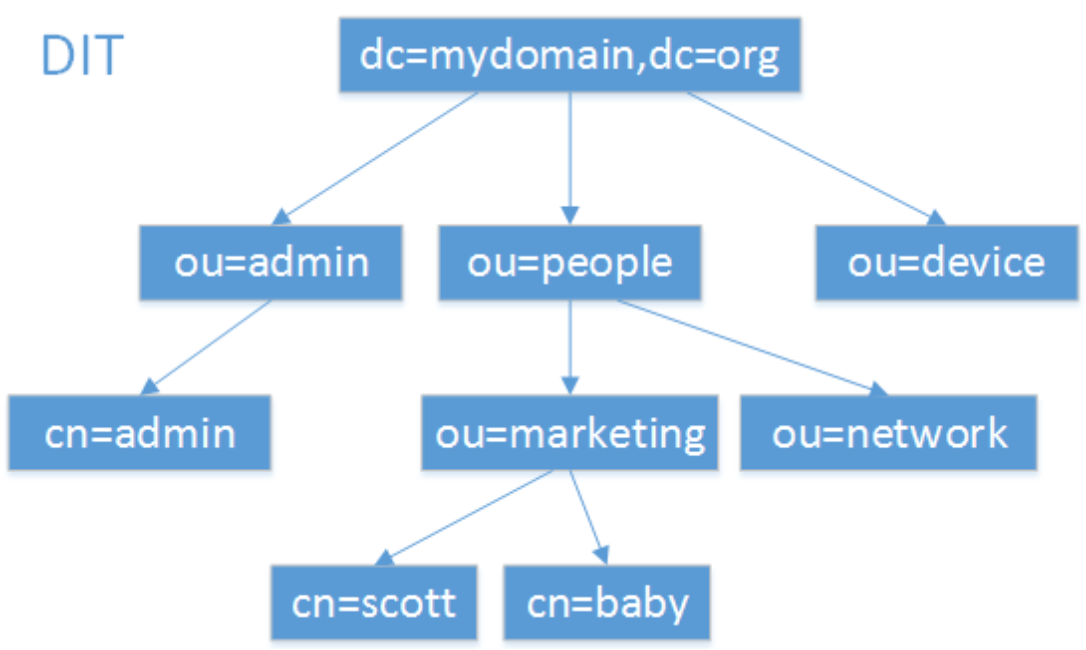
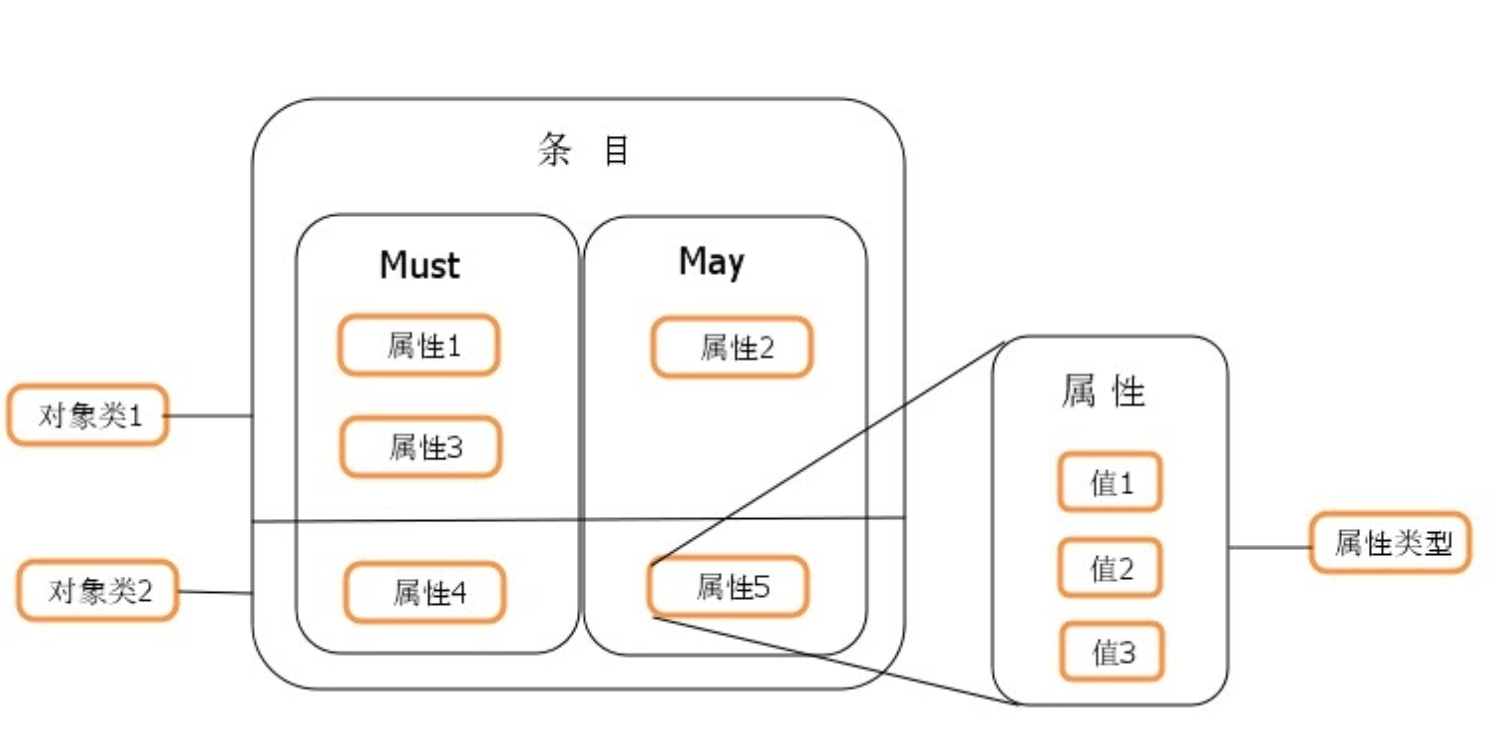
概念 目录树 在一个目录服务系统中,整个目录信息集可以表示为一个目录信息树,树中的每个节点是一个条目。
Entry条目 也叫记录项,是LDAP中最基本的颗粒,就像字典中的词条,或者是数据库中的记录。通常对LDAP的添加、删除、更改、检索都是以条目为基本对象的。每个条目有自己的唯一可区别的名称(DN)。
关键字 英文全称 含义
dn Distinguished Name
“uid=songtao.xu,ou=oa,dc=example,dc=com”,一条记录的位置(唯一)
Base DN LDAP目录树的最顶部就是根,也就是所谓的“Base DN”,如”dc=mydomain,dc=org”。
rdn Relative dn
一般指dn逗号最左边的部分,,如cn=baby。它与RootDN不同,RootDN通常与RootPW同时出现,特指管理LDAP中信息的最高权限用户。
dc Domain Component
domain component,常用来指一个域名的一部分,如域名为example.com变成dc=example,dc=com(一条记录的所属位置)
Attribute属性: 描述条目的某个方面的信息,一个属性由一个属性类型和一个或多个属性值组成,属性有必须属性和非必须属性。
关键字 英文全称 含义
uid User Id
用户ID songtao.xu(一条记录的ID)
ou Organization Unit
一个组织单元的名字,如“oa组”(一条记录的所属组织)
cn Common Name
common name,一个对象的名字,如果指人,使用全名
sn Surname
姓,如“许”
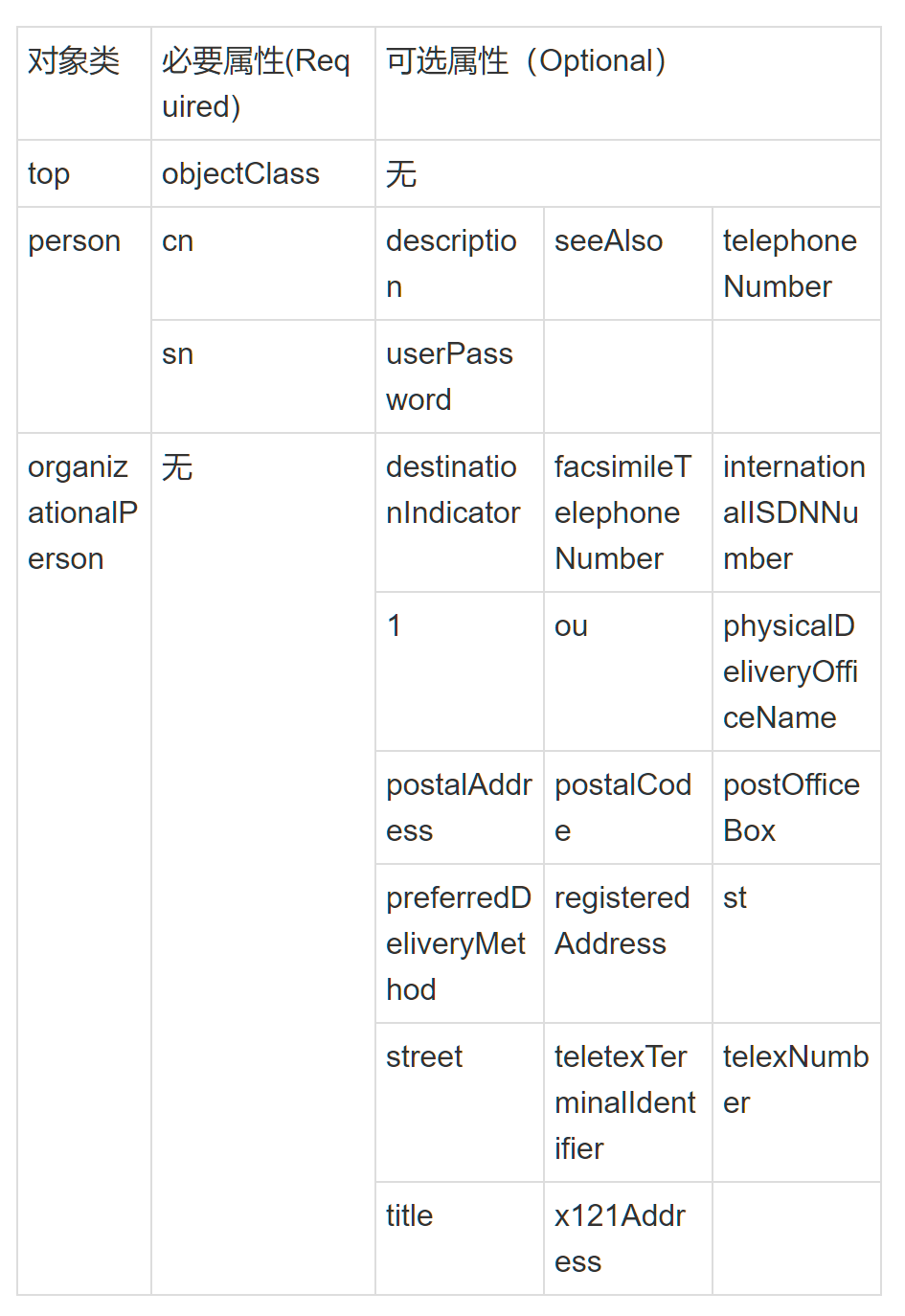
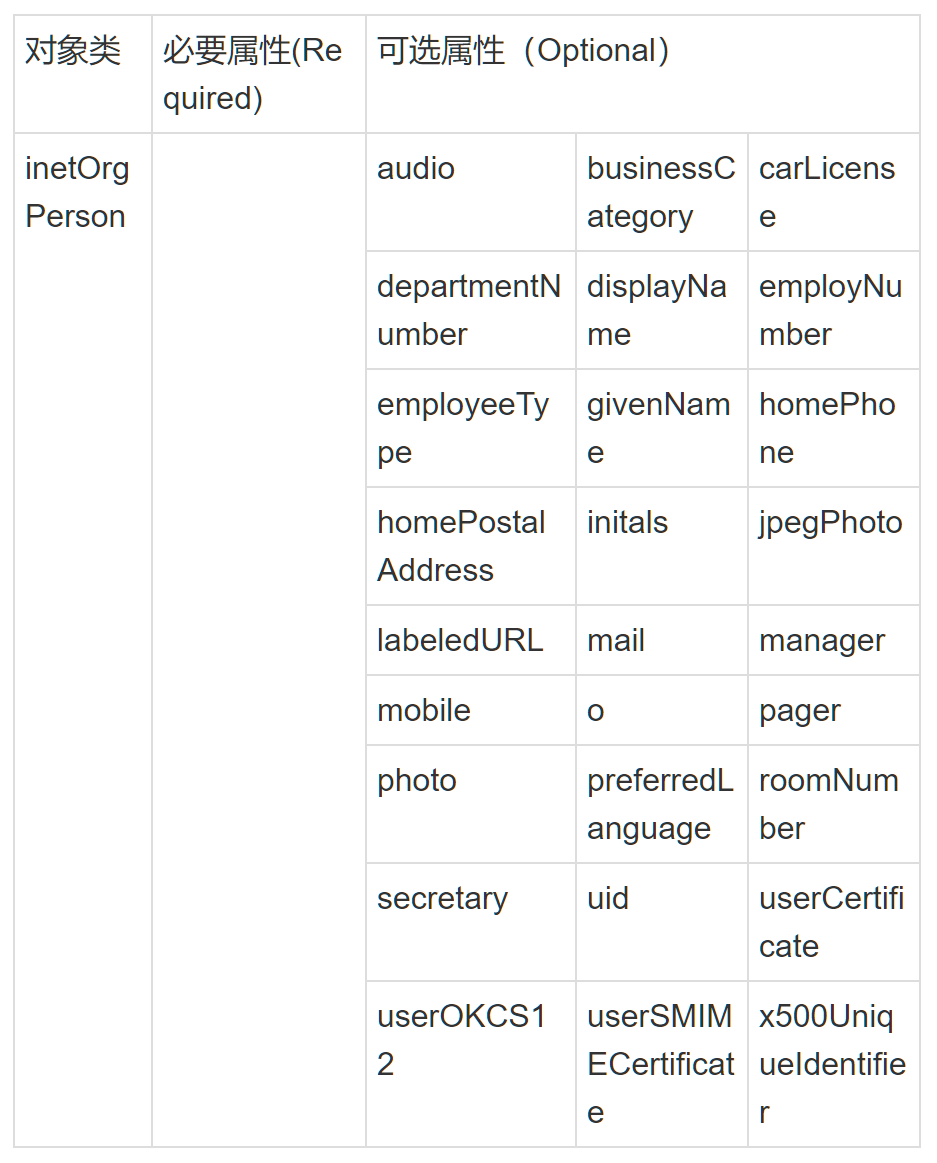
ObjectClass对象类 与某个实体类型对应的一组属性,对象类是可以继承的,这样父类的必须属性也会被继承下来。
在LDAP中,一个条目必须包含一个Oject class属性,且需要赋予至少一个值。
Schema 对象类(ObjectClass)、属性类型(AttributeType)、语法(Syntax)分别约定了条目、属性、值,他们之间的关系如下 图所示。所以这些构成了模式(Schema)——对象类的集合。条目数据在导入时通常需要接受模式检查,它确保了目录中所有的条目数据结构都是一致的。
schema(一般在/etc/ldap/schema/目录)在导入时要注意前后顺序。
TLS & SASL 分布式LDAP 是以明文的格式通过网络来发送信息的,包括client访问ldap的密码(当然一般密码已然是二进制的),SSL/TLS 的加密协议就是来保证数据传送的保密性和完整性。
SASL (Simple Authenticaion and Security Layer)简单身份验证安全框架,它能够实现openldap客户端到服务端的用户验证,也是ldapsearch、ldapmodify这些标准客户端工具默认尝试与LDAP服务端认证用户的方式(前提是已经安装好 Cyrus SASL )。SASL有几大工业实现标准:Kerberos V5、DIGEST-MD5、EXTERNAL、PLAIN、LOGIN。
Kerberos V5是里面最复杂的一种,使用GSSAPI机制,必须配置完整的Kerberos V5安全系统,密码不再存放在目录服务器中,每一个dn与Kerberos数据库的主体对应。DIGEST-MD5稍微简单一点,密码通过 saslpasswd2生成放在sasldb数据库中,或者将明文hash存到LDAP dn的userPassword中,每一个authid映射成目录服务器的dn,常和SSL配合使用。参考将 LDAP 客户端配置为使用安全性
EXTERNAL一般用于初始化添加schema时使用,如ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/core.ldif。
LDIF LDIF(LDAP Data Interchange Format,数据交换格式)是LDAP数据库信息的一种文本格式,用于数据的导入导出,每行都是“属性: 值”对,见 openldap ldif格式示例
OpenLDAP(2.4.3x)服务器安装配置方法见这里 。
使用 修改根DN与添加密码 1 2 3 4 5 6 7 8 9 10 11 $ vim /etc/openldap/slapd.d/cn\=config/olcDatabase\=\{2\}hdb.ldif olcSuffix: dc=quhui,dc=com olcRootDN: cn=root,dc=quhui,dc=com olcRootPW: {SSHA}cQb7UUcz2x6p6rB1gm9EmsVcM8Rrfp6h $ vim /etc/openldap/slapd.d/cn\=config/olcDatabase\=\{1\}monitor.ldif dn.base="cn=Manager,dc=my-domain,dc=com" $ systemctl start slapd
解决无法操作根节点数据This base cannot be created with PLA问题 1 2 3 4 5 6 7 $ cat > base.ldif << EOF dn: dc=quhui,dc=com o: ldap objectclass: dcObject objectclass: organization EOF $ ldapadd -f base.ldif -x -D cn=root,dc=quhui,dc=com -W
导入管理员帐号信息 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 cat > root.ldif << EOF dn: dc=quhui,dc=com o: quhui com dc: quhui objectClass: top objectClass: dcObject objectclass: organization dn: cn=root,dc=quhui,dc=com cn: root objectClass: organizationalRole description: Directory Manager dn: ou=People,dc=quhui,dc=com ou: People objectClass: top objectClass: organizationalUnit dn: ou=Group,dc=quhui,dc=com ou: Group objectClass: top objectClass: organizationalUnit EOF $ ldapadd -x -D "cn=root,dc=quhui,dc=com" -W -f /root/root.ldif
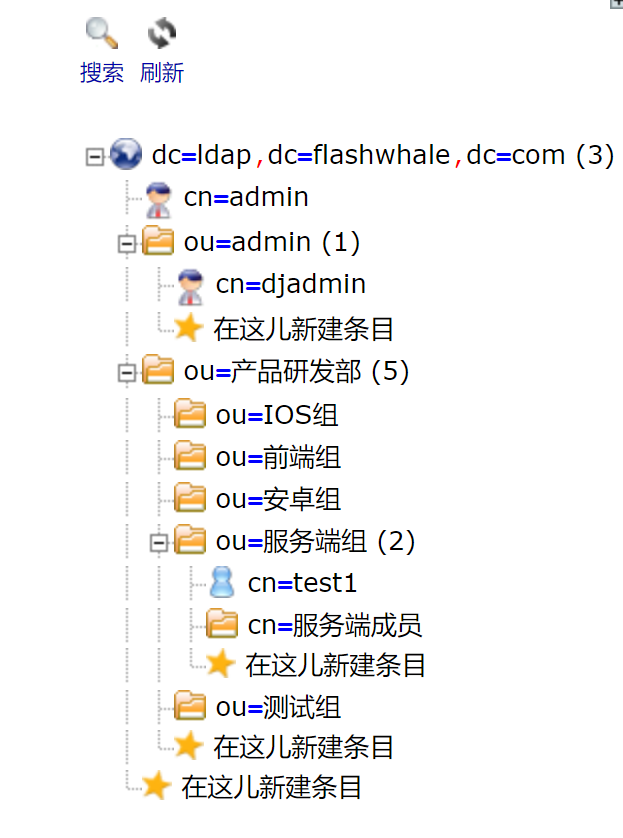
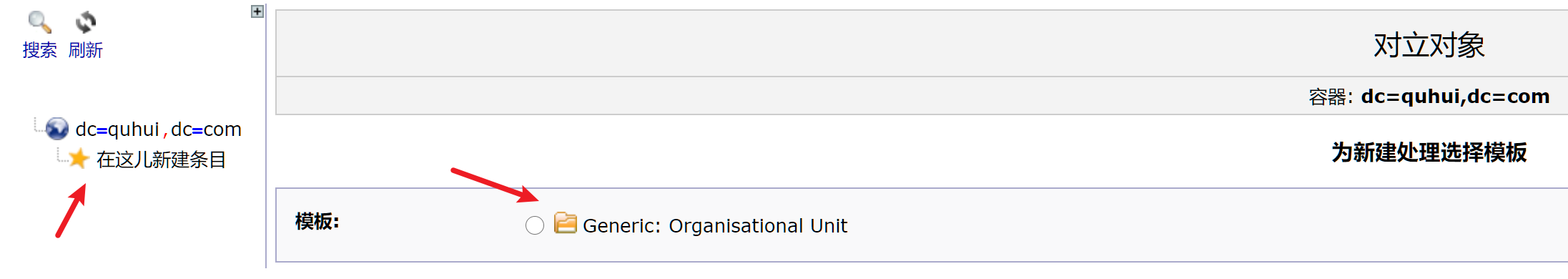
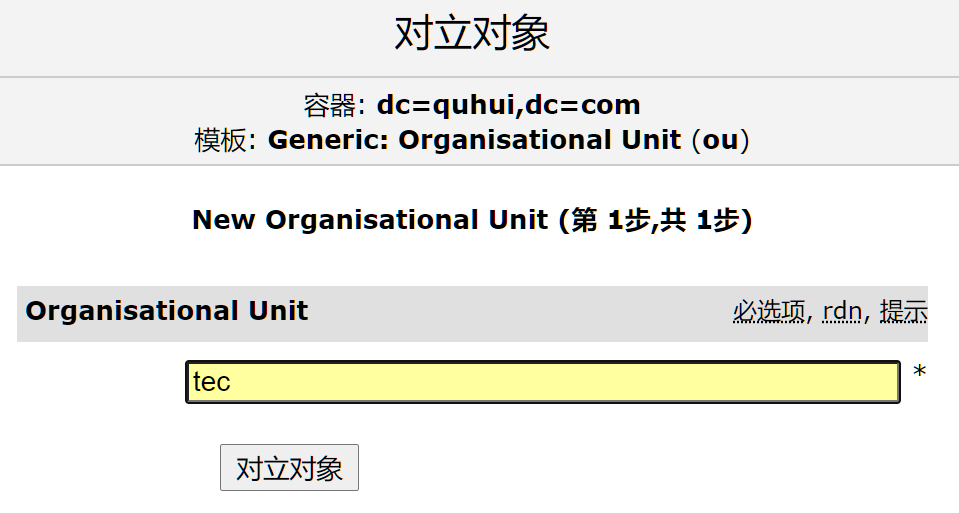
新建OU
新建OU后就可以用界面新建组与用户了
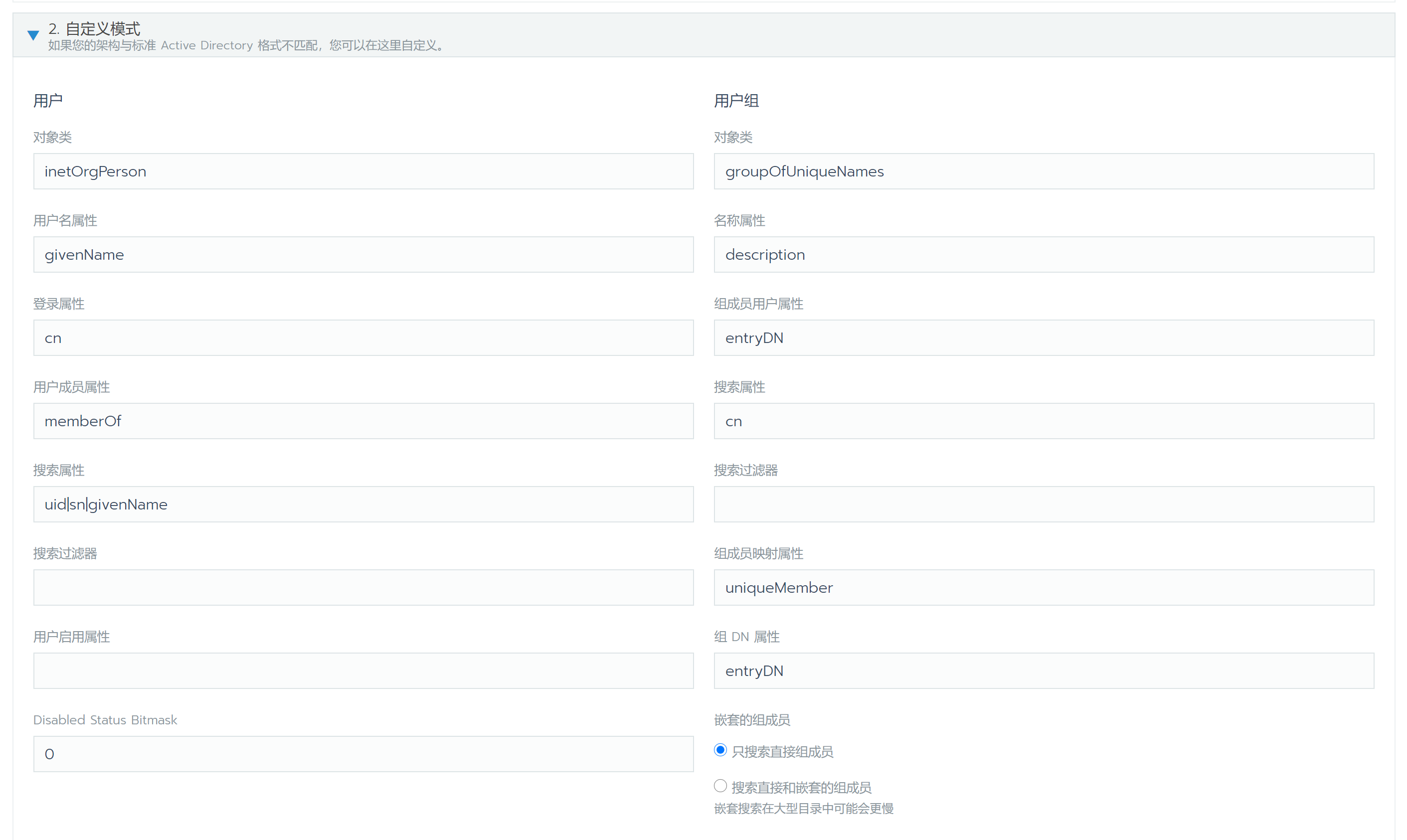
GroupOfUniqueNames用户组属性 添加配置
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 cat > memberof_config.ldif << EOF dn: cn=module,cn=config cn: module objectClass: olcModuleList olcModuleLoad: memberof olcModulePath: /usr/lib64/openldap dn: olcOverlay=memberof,olcDatabase={2}hdb,cn=config objectClass: olcConfig objectClass: olcMemberOf objectClass: olcOverlayConfig objectClass: top olcOverlay: memberof olcMemberOfDangling: ignore olcMemberOfRefInt: TRUE olcMemberOfGroupOC: groupOfUniqueNames olcMemberOfMemberAD: uniqueMember olcMemberOfMemberOfAD: memberOf EOF cat > refint1.ldif << EOF dn: cn=module{1},cn=config add: olcmoduleload olcmoduleload: refint EOF cat > refint2.ldif << EOF dn: olcOverlay=refint,olcDatabase={2}hdb,cn=config objectClass: olcConfig objectClass: olcOverlayConfig objectClass: olcRefintConfig objectClass: top olcOverlay: refint olcRefintAttribute: memberof uniqueMember manager owner EOF sudo ldapadd -Q -Y EXTERNAL -H ldapi:/// -f memberof_config.ldif sudo ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f refint1.ldif sudo ldapadd -Q -Y EXTERNAL -H ldapi:/// -f refint2.ldif
导入用户组
1 2 3 4 5 6 7 8 9 cat > group1.ldif << EOF dn: cn=yunweizu,ou=Group,dc=quhui,dc=com objectClass: groupOfUniqueNames objectClass: top cn: yunweizu description: 运维组 uniqueMember: uid=test,ou=People,dc=quhui,dc=com EOF $ ldapadd -x -w "123456" -D "cn=root,dc=quhui,dc=com" -f /root/group1.ldif
1 2 $ ldapsearch -x -LLL -H ldap://127.0.0.1 -x -D "cn=root,dc=quhui,dc=com" -w "123456" -b uid=quhui,ou=People,dc=quhui,dc=com dn uniqueMember dn: uid=quhui,ou=People,dc=quhui,dc=com
生成新配置文件 1 2 3 4 5 6 7 8 9 10 11 rm -rf /etc/ openldap/slapd.d.bak cp -a /etc/ openldap/slapd.d / etc/openldap/ slapd.d.bak rm -rf /etc/ openldap/slapd.d/ * slapadd -n 0 -F /etc/ openldap/slapd.d -l /u sr/share/ openldap-servers/slapd.ldif ldapadd -Y EXTERNAL -H ldapi:// / -f / etc/openldap/ schema/cosine.ldif ldapadd -Y EXTERNAL -H ldapi:// / -f / etc/openldap/ schema/nis.ldif ldapadd -Y EXTERNAL -H ldapi:// / -f / etc/openldap/ schema/inetorgperson.ldif chown -R ldap.ldap /etc/ openldap/* chown -R ldap.ldap /var/ lib/ldap/ * systemctl restart slapd
添加用户及用户组 命令
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 $ cat << EOF | ldapadd -x -D cn=root,dc=quhui,dc=com -W dn: dc=quhui, dc=com dc: quhui objectClass: top objectClass: domain dn: ou=people, dc=quhui, dc=com ou: people objectClass: top objectClass: organizationalUnit dn: ou=group, dc=quhui, dc=com ou: group objectClass: top objectClass: organizationalUnit EOF Enter LDAP Password: adding new entry "dc=quhui, dc=com" adding new entry "ou=people, dc=quhui, dc=com " adding new entry "ou=group, dc=quhui, dc=com"
文件
新建test11.ldif 写入以下内容
1 2 3 4 5 6 7 8 9 10 11 12 13 dn: dc=flashwhale,dc=com objectClass: top objectClass: person objectClass: posixAccount objectClass: shadowAccount uid: test11 cn: test11 sn: test11 uidNumber: 1034 gidNumber: 1003 loginShell: /bin/bash homeDirectory: /home/test11/
创建ldap用户
1 ldapadd -x -H ldap://127.0.0.1:389 -D "cn=admin,dc=flashwhale,dc=com" -w djadmin -f /root/test11.ldif
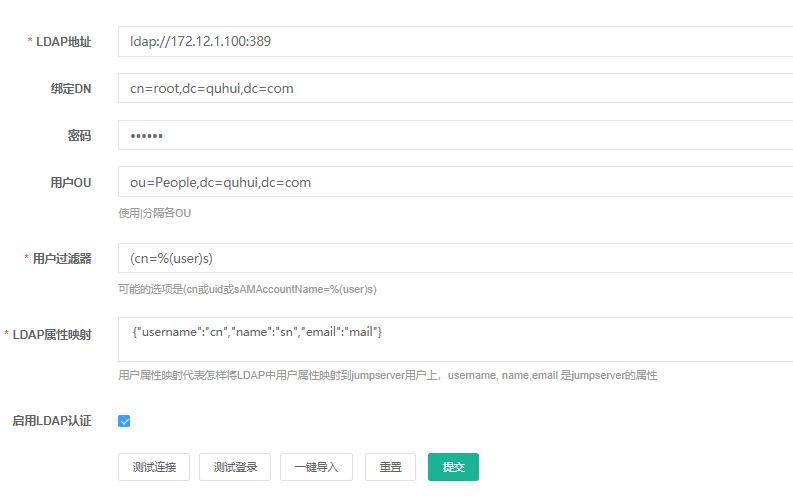
ldapadmin 对接 jumpserver 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 docker run -d --name jumpserver -h jumpserver --restart =always \ -v /data/jumpserver:/opt/jumpserver/data/media \ -p 8080:80 \ -p 2222:2222 \ -e SECRET_KEY =123456 \ -e BOOTSTRAP_TOKEN =123456 \ -e DB_HOST =172.12.1.100 \ -e DB_PORT =3306 \ -e DB_USER =root \ -e DB_PASSWORD ="123456" \ -e DB_NAME =jumpserver \ -e REDIS_HOST =172.12.1.100 \ -e REDIS_PORT =6379 \ -e REDIS_PASSWORD ="123456" \ jumpserver/jms_all:v2.4.4
测试连接–> 提交–>测试登录–>一键导入
jumpserver只导入用户,组管理在内部实现
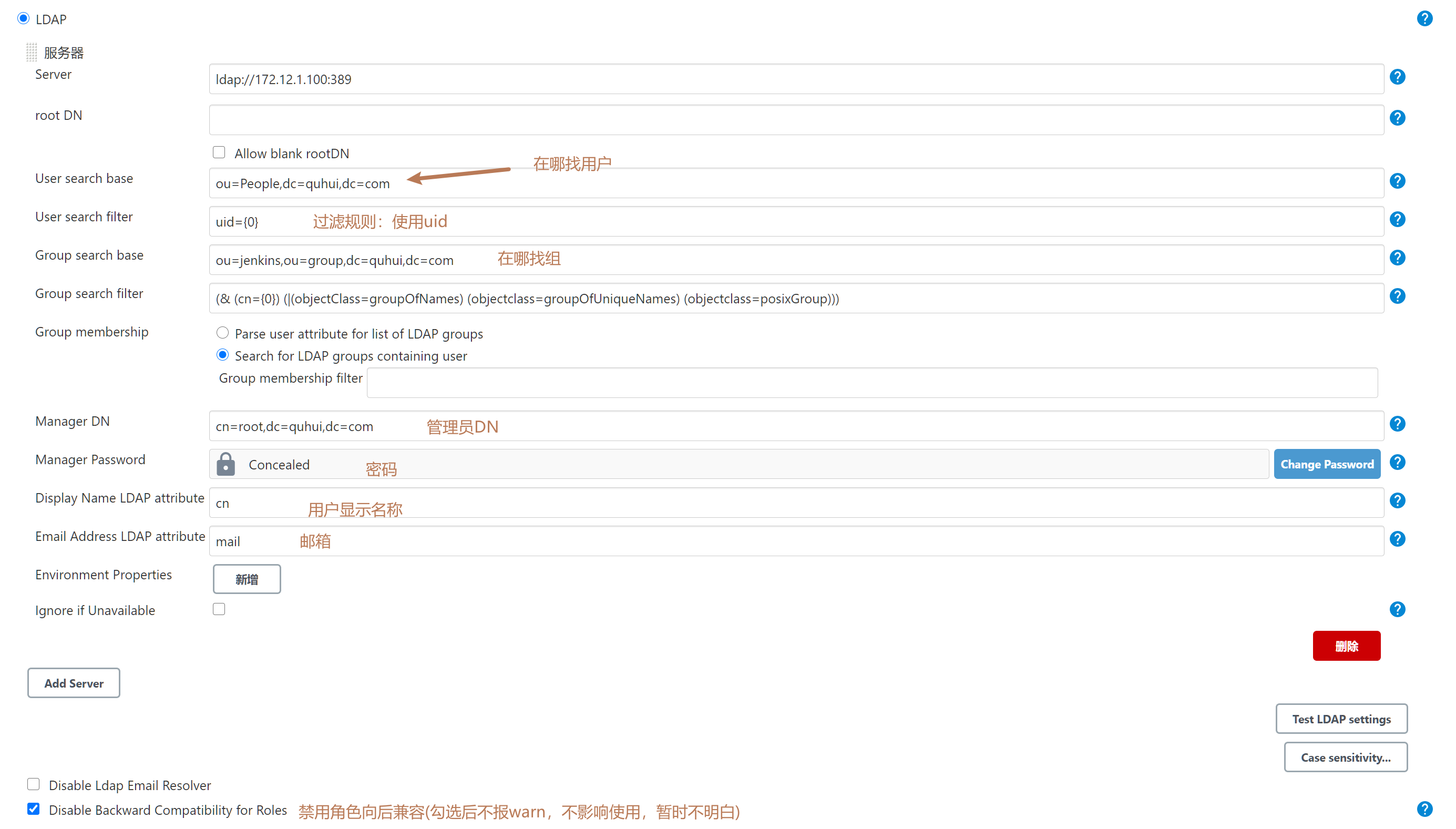
jenkins 1 2 3 4 5 6 7 8 9 10 11 12 docker run -d \ -p 8000 :8080 -p 50000 :50000 \ --net=host \ --name jenkins \ -v /data/ jenkins_home:/var/ jenkins_home \ -v /var/ run/docker.sock:/ var/run/ docker.sock \ -v /usr/ bin/docker:/u sr/bin/ docker \ -v /etc/ localtime:/etc/ localtime \ -v /etc/ localtime:/etc/ localtime \ --privileged=true \ -e JAVA_OPTS="-Duser.timezone=Asia/Shanghai -Dfile.encoding=utf-8" \ registry.cn-hangzhou.aliyuncs.com/xqbl-share/ jenkins_root:2.235 .2 -lts-centos7
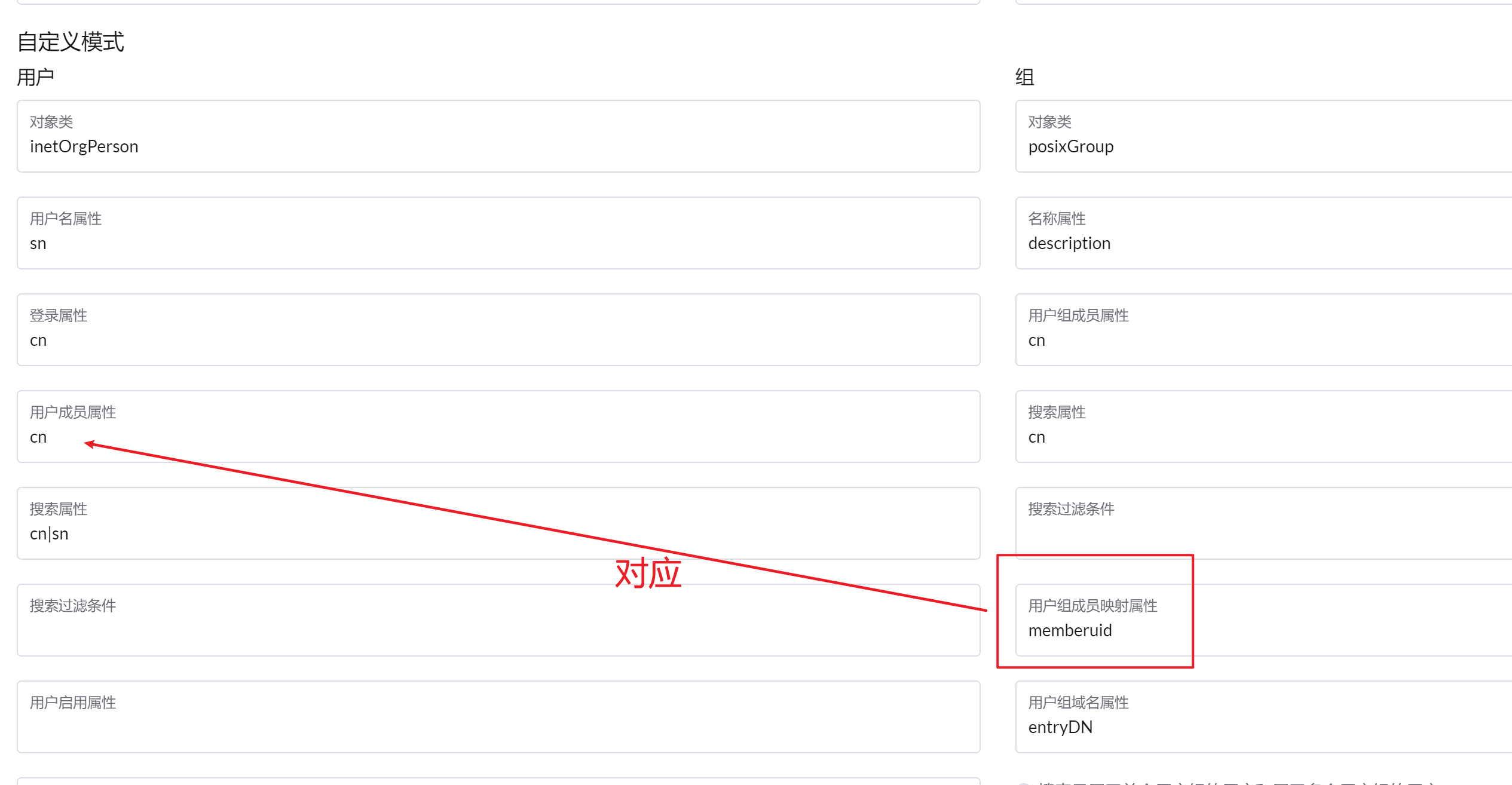
1 (& cn= {0 }) (|(objectClass=groupOfNames ) (objectclass=groupOfUniqueNames ) (objectclass=posixGroup )))
rancher