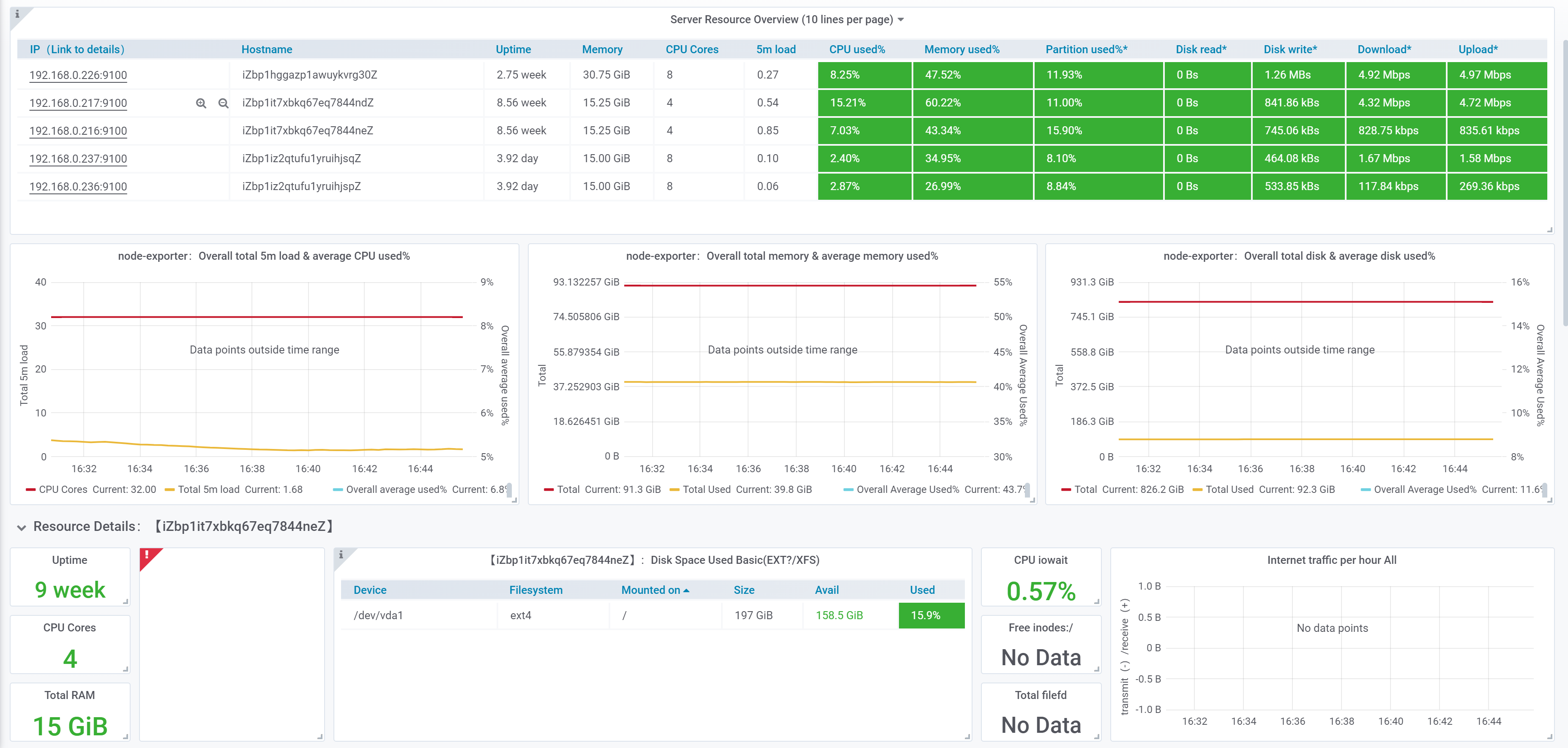
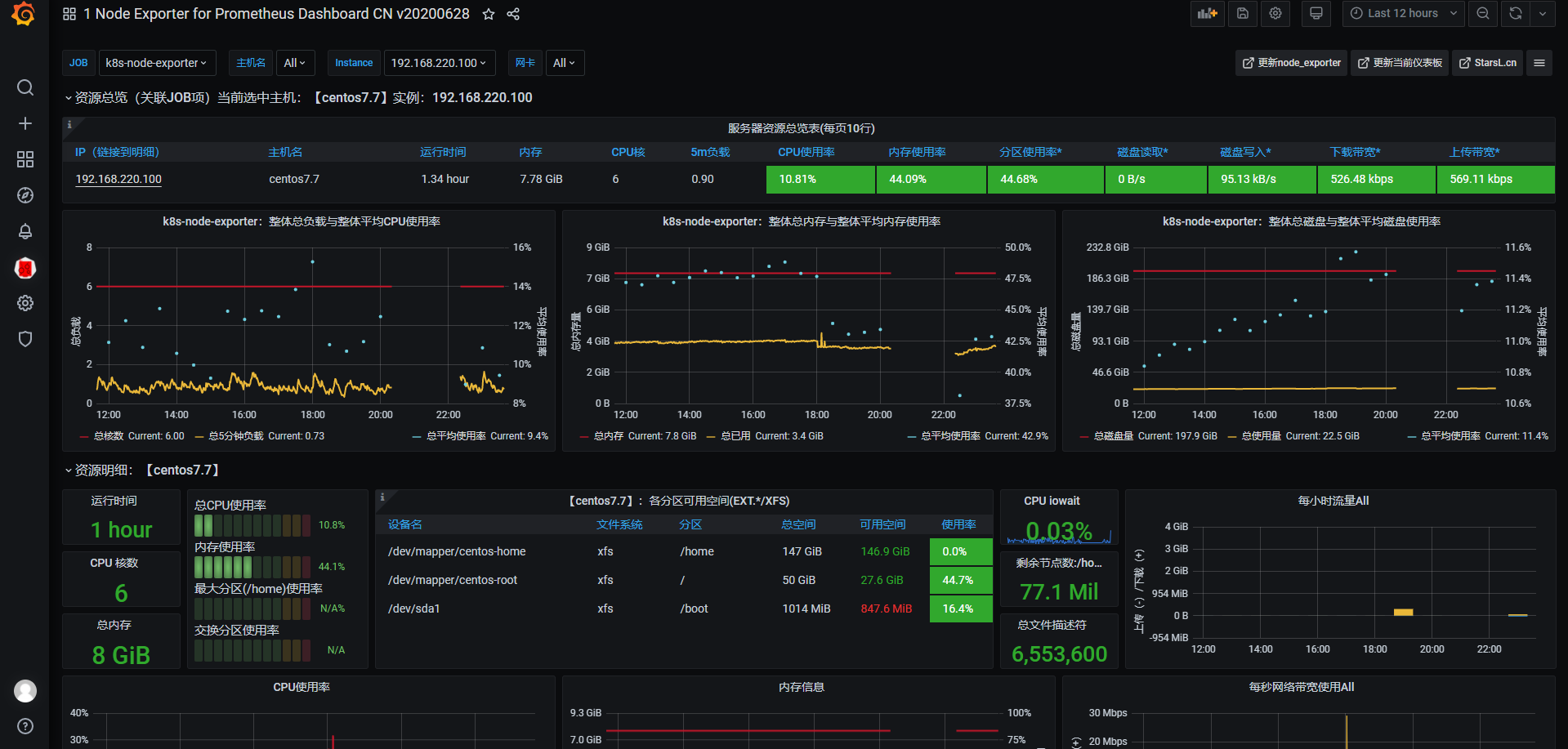
容器JVM限制
早期时候,容器内运行Java应用程序时,Jvm无法感知容器环境存在,所以对容器资源的限制比如内存或者cpu等都无法生效。
原因是容器的资源管理使用了操作系统cgroup机制,但是Jvm无法感知cgroup。
所以可能需要在jvm以及docker中指定两次内存限制。
后来,在Jvm9及以后,Jvm开始了对容器资源限制的支持。在Jvm11中,可以使用-XX:+UseContainerSupport参数来制定Jvm使用容器内存。
另外还有两个参数-XX:InitialRAMPercentage -XX:MaxRAMPercentage来制定Jvm使用容器内存的百分比。
1 | -XX:+UseContainerSupport #开启容器支持 |
1 | jinfo -flags pid #查看启动参数 |